9447 2015 / Recon 1
November 29, 2015
Description
Someone has attacked your site. We have attached a log collected from the time of the attack.
This task is split into two parts. The end goal (Recon 2) is to find the full name of the attacker.
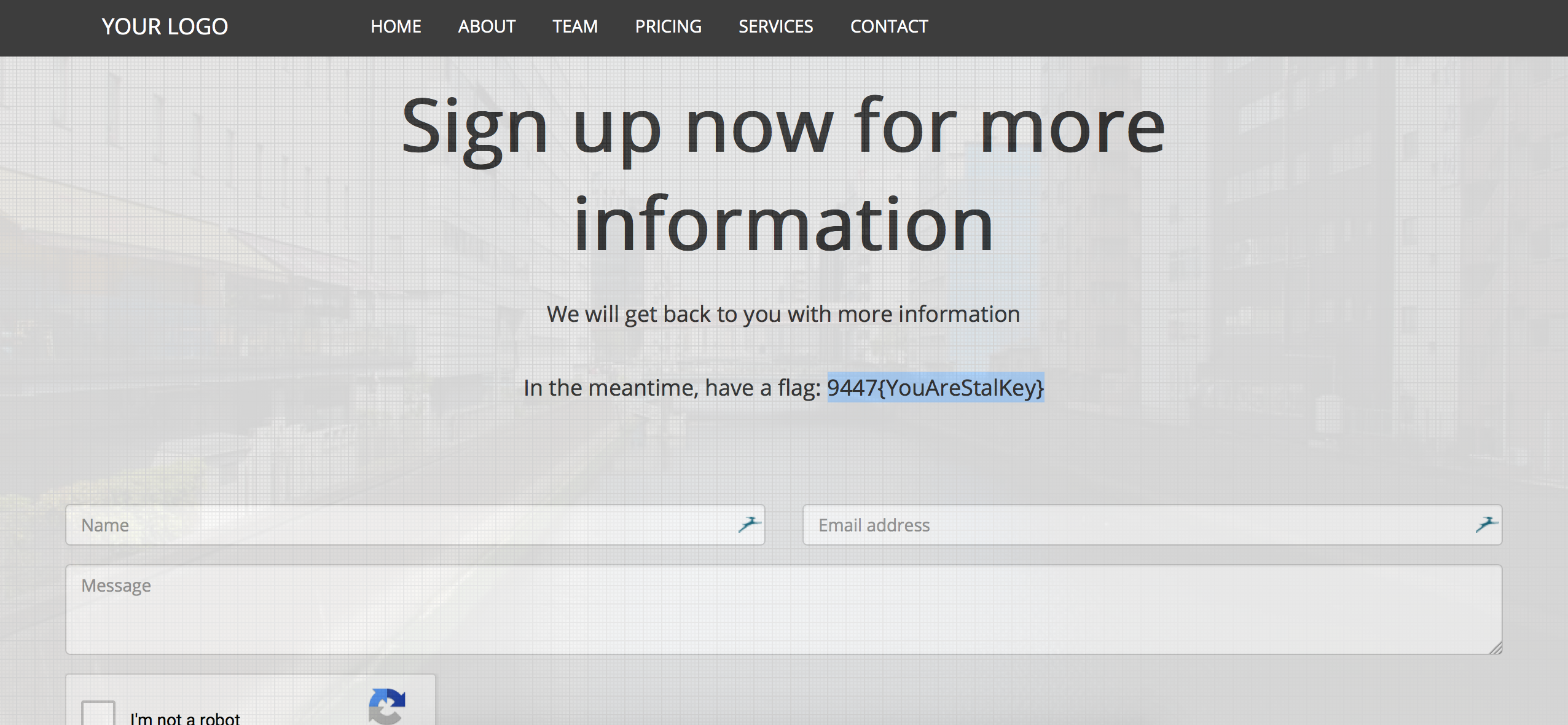
Hint : The flag for Recon 1 is not the name of the attacker. Recon 1 flag will appear as 9447{…} on your screen when you find it.
Challenge Files
The Challenge
The goal of this challenge was to find out who attacked your website.
The challenge came with a log file containing all the requests sent to your fictional website, including IPs and timestamps :
192.241.254.77 - - [15/Nov/2015:16:01:32 +0000] "GET /admin HTTP/1.1" 403 283 "-" "curl/7.35.0"
[ ... ]
37.139.17.15 - - [15/Nov/2015:16:28:03 +0000] "POST /login HTTP/1.1" 200 5613 "-" "Python-urllib/2.7"
37.139.17.15 - - [15/Nov/2015:16:28:04 +0000] "POST /login HTTP/1.1" 200 5613 "-" "Python-urllib/2.7"
37.139.17.15 - - [15/Nov/2015:16:28:05 +0000] "POST /login HTTP/1.1" 200 5613 "-" "Python-urllib/2.7"
37.139.17.15 - - [15/Nov/2015:16:28:06 +0000] "POST /login HTTP/1.1" 200 5613 "-" "Python-urllib/2.7"
37.139.17.15 - - [15/Nov/2015:16:28:06 +0000] "POST /login HTTP/1.1" 200 5613 "-" "Python-urllib/2.7"
37.139.17.15 - - [15/Nov/2015:16:28:07 +0000] "POST /login HTTP/1.1" 200 5613 "-" "Python-urllib/2.7"
37.139.17.15 - - [15/Nov/2015:16:28:08 +0000] "POST /login HTTP/1.1" 200 5613 "-" "Python-urllib/2.7"
37.139.17.15 - - [15/Nov/2015:16:28:09 +0000] "POST /login HTTP/1.1" 200 5613 "-" "Python-urllib/2.7"
37.139.17.15 - - [15/Nov/2015:16:28:10 +0000] "POST /login HTTP/1.1" 200 5613 "-" "Python-urllib/2.7"
192.241.254.77 - - [15/Nov/2015:16:28:11 +0000] "GET /admin HTTP/1.1" 200 283 "-" "curl/7.35.0"
The list consisted of two attackers 37.139.17.15 and 192.241.254.77.
The interesting one was 192.241.254.77 as it was the only IP that generated a 200 response from the /admin page.
Browsing to that IP reveals nothing but a plain text “go away” message :
$ curl http://192.241.254.77/
go away
A reverse lookup of the IP reveals www.williestoleyour.pw :
$ nslookup 192.241.254.77
Server: 10.10.10.10
Address: 10.10.10.10#53
Non-authoritative answer:
77.254.241.192.in-addr.arpa name = www.williestoleyour.pw.
Authoritative answers can be found from:
. nameserver = d.root-servers.net.
. nameserver = e.root-servers.net.
. nameserver = i.root-servers.net.
[ ... ]
Not much to go on here, nothing in the source code and searches through dnsdumpster and w3dt didn’t reveal much.
The contact section had the following email : info@williestoleyour.pw
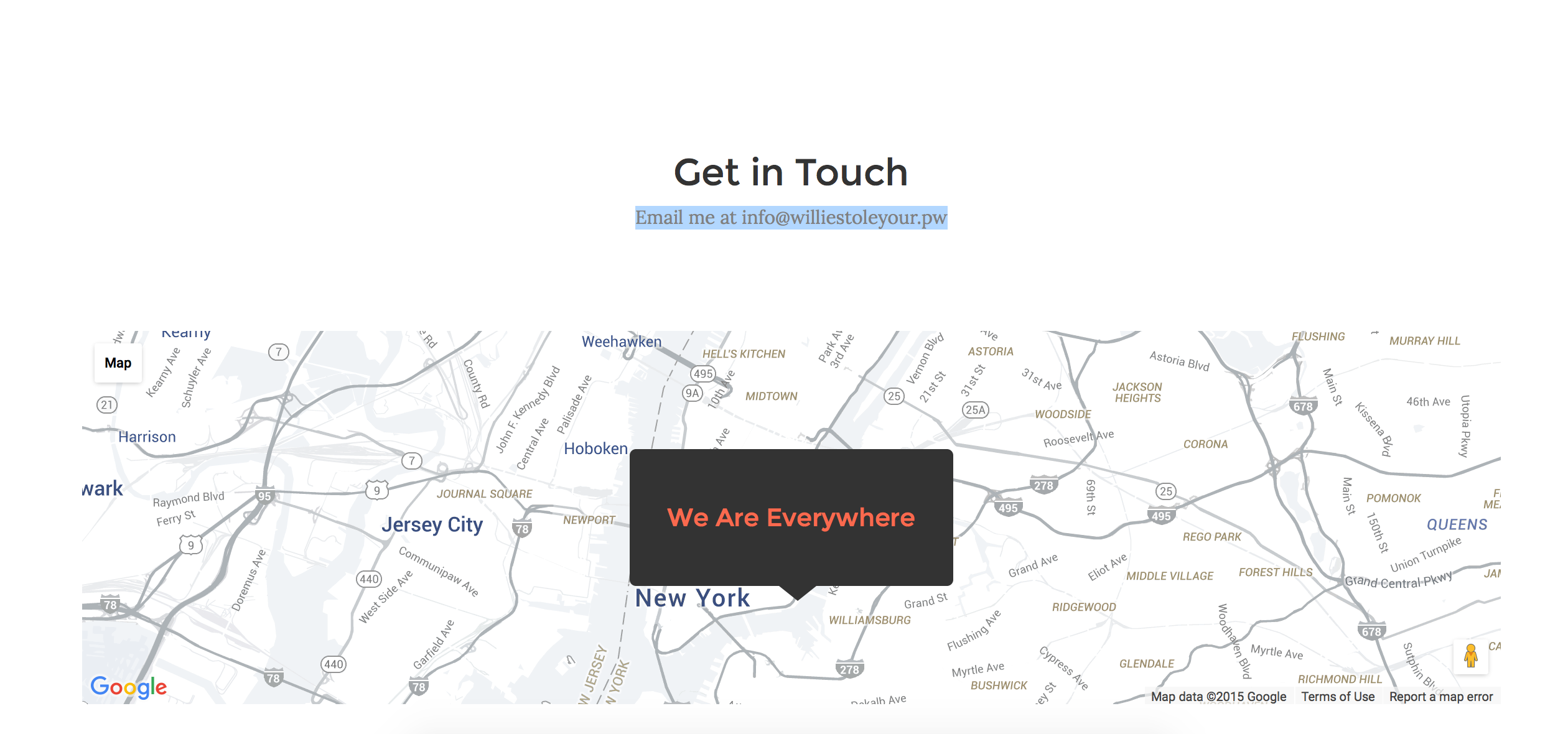
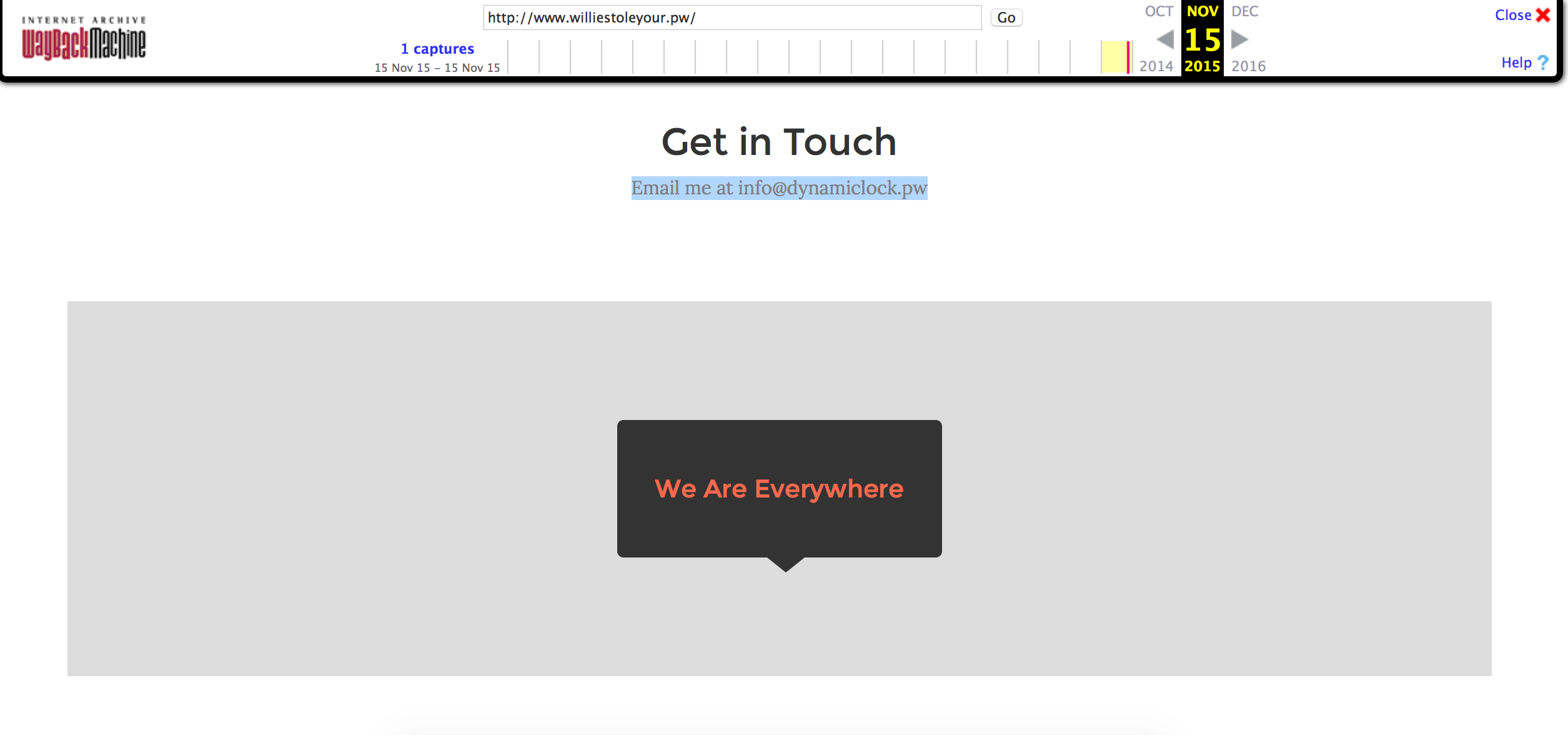
A search through the Wayback Machine reveals the same website with a different email info@dynamiclock.pw:
Visit dynamiclock.pw and scroll to the bottom and you’ll find your flag!